Object Oriented Distributed Virtual Systems Framework (2004)
(OODVS Framework, Intelligent Handlers, Proxy Methods, Threaded Methods, Migratory Objects, Distributed System, Shared State)
Diego Malpica Chauvet et al.
okc.mx,
diego-malpica@openknowledge.mx
| |
OODVS is a framework that is focused on using advanced object oriented features to reduce the complexity of distributed systems. |
|
 Abstract
Abstract
OODVS is a "Object Oriented Distributed Virtual Systems Framework" that is focused on using advanced object oriented features to reduce the complexity of distributed systems.
1 Introduction
Originally, the development of Distributed Virtual Reality was strongly promoted by the military industry, mainly for the elaboration of combat simulators. This industry has devoted a lot of resources to developing quality software allowing for reuse compatibility and portability of components, emphasizing the protection of previous investment. Today, the development of virtual reality is more diverse, due to develop in new areas such as entertainment, medicine and manufacturing. Many new technologies have been arrived since DIS(Distributed Interactive Simulation) protocol origin in in 1980.
Figure 1: Technology advances 1972-2013
Shared state maintenance is governed by the Consistency-Throughput Trade-off that imposes physical limits on how consistent state can be achieved within the given a set of constraints. Shared state is a complex issue. Selecting an appropriate shared state maintenance technique is an engineering task that must balance a variety of issues, including bandwidth, computation, latency, data consistency, and reproduce-ability.
There are three broad types of shared state maintenance:
Shared repository: Uses a centralized database to store the net current state. It provides highly consistent state maintenance at the expense of high bandwidth, slow throughput, and tight inter-dependencies among participating hosts.
Blind broadcast: Transmits updates on a regular basis. Sacrifices absolute consistency in favor of eventual consistency while reducing the inter-dependencies among participating hosts.
Dead reckoning: Transmits non-regular updates and uses prediction and convergence to manage state at remote hosts. Provides weakly consistent state maintenance (bounded error) in order to minimize bandwidth and maximize host autonomy.
2 Technologies
2.1 Java Platform
The language is a key factor to our approach since the power of expression is directly related with the external complexity. To see the language as the center of integration of multiple technologies (as a platform) it really simplifies things just take a glance to the following table that’s shows the relevant technologies for our point of view integrated to the java platform.
|
Version
|
Technologies
|
|
Java 1.0
|
Object Oriented, Virtual Machine, Threads, Sockets, Garbage Collection, Dynamic Loading
|
|
Java 1.1
|
Just in time compilation, Serialization, Remote Method Invocation, Reflection
|
|
Java 1.2
|
Cryptography
|
|
Java 1.3
|
Proxies
|
|
Java 1.4
|
XML
|
|
Java 1.5
|
Annotations, Concurrency, Generics
|
Table 1: Java Platform relevant technologies
2.2 Remote Methods
RMI (Remote Method Invocation) has been part of the Java Platform since version 1.2 unfortunately the current implementation has not fully take advantage of platform advances like reflection (proxy, annotations), and protocols (HTTP, UDP Broadcast, UDP Multicast).
Since we consider this technology a key factor we have implemented our own remote method stack which it provides a kind of RMI, RPC services that doesn’t need stubs, skeletons or an external tool. Currently we support various protocols implemented over HTTP/TCP and UDP (Broadcast and Multicast) and they have several security features based on Bouncy Castle Cryptography API. The semantics are very similar to the RMI semantics, but designed to support the implementation of the Proxy Model that we will see ahead.
2.3 Intelligent Handlers
Handlers could be seen as a kind of proxy that it’s placed between method invocations and the method execution. A handler in conjunction with other java features as reflection an annotation, can greatly simplify the design and the semantics of the components. We used handlers to implement our remote method stack with out the need of external tools and precompiled stubs or skeletons. We also used handler to implement the Proxy Model.
2.4 Proxy Model
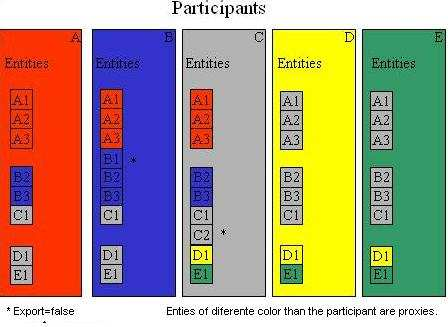
The purpose of the model is to support objects and messages distribution. The model is constituted by three roles: Participant Entity and Proxy. The interaction between these roles defines a Distributed Virtual System.
2.4.1 Role responsibilities
Participant
- Holds the entities
- Interact with entities to update their proxies
- Interact with the proxies to update states
- Interact with other participants to distribute proxies
- Propagate proxies between regions
- Send heart beats to publish himself to other participants.
- Listen for other participants hear beats.
- Remove dead assumed participants
- Send proxies of new entities to known participants
- Send proxies of its entities to new known participants
- Provides classes and resources to other participants
Entity
- Contains state information
- Contains references to its proxy entities
- Contains methods and Proxy methods
Proxy
- Is an entity that’s has a parent entity.
- Contains a reference to a root entity.
- Could be the parent of other proxy entities.
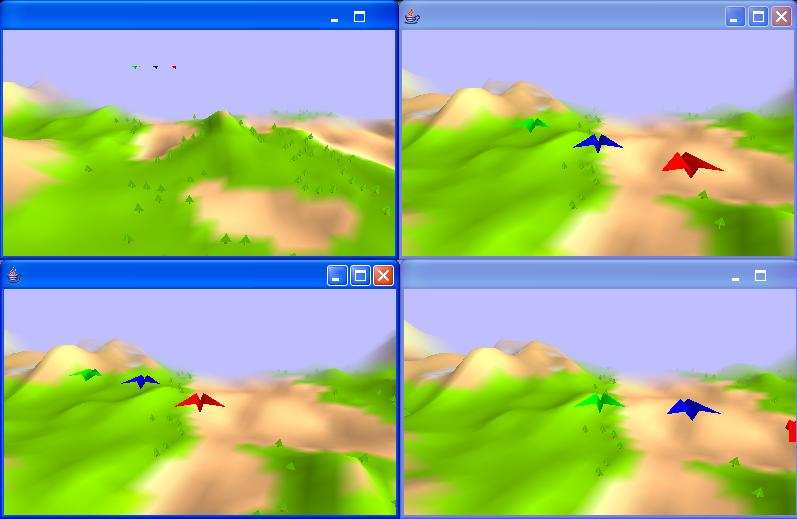
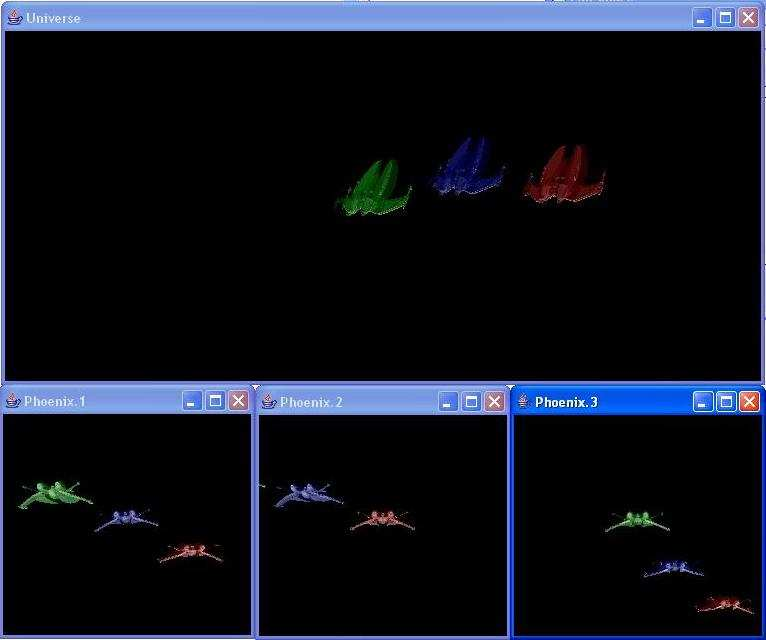
Figure 2: Planes implemented using our Proxy Model and OpenGL, every window is a different participant; each participant sees its entities and the proxies from other participant’s entities.
Figure 3: Illustrates the object distribution between five participants
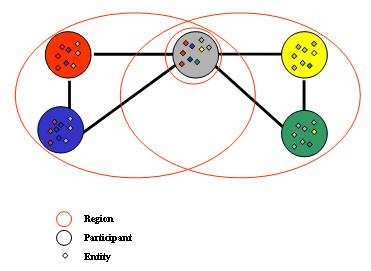
Figure 4: Illustrates different visibility regions between the five participants of the figure 2.
2.5 Proxy Methods
Proxy methods are implemented via Handlers and they are used to propagate messages to the entities and all its proxies.
2.6 Time Perception
The time services allow to have different times and clock speeds and to mitigate network latency effects. They are used in conjunction with prediction and convergence algorithms like the Dead reckoning implemented in advanced examples.
2.7 Dead Reckoning
The Proxy model eases the implementation of Predictive and Convergence algorithms the Proxy Model is a kind of dead reckoning general implementation.
2.8 Security
We base our solution cryptography in the Bouncy Castle Light-weight API.
2.9 Migratory Objects
Full objects (code and data) are moved between participants a participant can retrieve code and resources on demand from other participants.
3 Hands on Code
3.1 Remote Methods
These are the interface and class for the object to be used for remote method invocation in the next code fragments.
public interface ObjectExample_I {
public String msg1(String name) throws Exception;
}
public class ObjectExample implements ObjectExample_I {
public String msg1(String str) {
System.out.println(str);
return "RE: "+ str ;
}
}
This is the server part; a remote method server is created and started. Then an object is created and added to the server to be ready for remote invocations.
RMServer server = new RMServer().start();
server.putObject("O1", new ObjectExample());
This is the client part; a handler is created and used to perform the remote method invocation.
RMClientContext cc = new RMClientContext("HTTP://localhost");
ObjectExample_I handler = (ObjectExample_I) cc.getHandler(ObjectExample_I.class, "O1");
String response = handler.msg1("Hello World.");
3.2 Remote Method Protocols
These are the interface and class for the object to be used for remote method invocation in the next code fragments.
public interface ObjectExample_I {
public String msg1(String name) throws Exception;
}
public class ObjectExample implements ObjectExample_I {
public String msg1(String str) {
System.out.println(str);
return "RE: "+ str ;
}
}
This is the server part. This code part first creates and initializes the server. If the keyDir and keys that does not exist it will be created.
UDP information is specified as part of the initialization for UDP remote method invocations. Finally the server is started.
An object is created and added to the server to be ready for remote method invocation.
|
FileUtils.mkdirs("keyDir");
RMServer server = new RMServer("keyDir", "masterPasswd", "serverPasswd");
server.setUDPPort(9001);
server.addCastAddress("224.0.0.1");
server.start();
server.putObject("O1", new ObjectExample());
|
This is the client part, a RMClientContext is created and used to obtain handlers to perform remote method invocations using various protocols.
|
RMClientContext context;
context = new RMClientContext("HTTP://localhost", RMClient.RM_HTTP_V1_0, "keyDir", "clientPasswd");
context.setUDPPort(9001);
context.addCastAddress("224.0.0.1");
ObjectExample_I handler;
handler = (ObjectExample_I) context.getHandler(RMClient.RM_V1_0,ObjectExample_I.class, "/O1");
handler.msg1("HTTP.");
handler = (ObjectExample_I) context.getHandler(RMClient.RM_UDP_V1_0, ObjectExample_I.class, "/O1");
handler.msg1("UDP.");
handler = (ObjectExample_I) context.getHandler(RMClient.RM_HTTP_SIG_V1_0, ObjectExample_I.class, "/O1");
handler.msg1("HTTP Signed.");
handler = (ObjectExample_I) context.getHandler(RMClient.RM_HTTP_SEC_V1_0, ObjectExample_I.class, "/O1");
handler.msg1("HTTP Signed and Encrypted.");
|
3.3 Proxy Model
These are the interface and the class used in the following code fragments.
Two proxy methods are implemented, with names terminated with TCPP an UDPP that stands for TCP Proxy method and UDP proxy method.
public interface EntityExample_I {
public void printMsg_TCPP(String msg) throws RMClientException;
public void printMsg_UDPP(String msg) throws RMClientException;
}
public class EntityExample extends Entity implements EntityExample_I {
public EntityExample(String name) throws RMClientException {
super(name);
}
public void printMsg_TCPP(String msg) throws RMClientException {
System.out.println(" Participant:" + getParticipantName() + " TCCP:" + msg);
}
public void printMsg_UDPP(String msg) throws RMClientException {
System.out.println(" Participant:" + getParticipantName() + " UUDP:" + msg);
}
}
The next fragment creates a participant "A" and adds a Entity "A1" to it.A proxy handler of entity "A1" is obtained.
The proxy handler is used to invoke the two proxy methods, the handler uses the prefix of the method name (UDPP, TCPP) to determine how to handle the method invocation.
Participant a = new Participant("A").start();
a.addEntity(new EntityExample("A1"));
EntityExample_I handler= (EntityExample_I) a.getHandler("A1",0);
handler.printMsg_UDPP("hello 1.");
handler.printMsg_TCPP("hello 2.");
The next fragment creates a participant "B".
Participants "A" and "B" will eventually discover each other and send proxies to each other.
After participant "B" is created a proxy for the entity "A1", will be retrieved.
Then the local method getName of the proxy will be invoked.
Finally a proxy handler for the proxy "A1" will be obtained.
Then the handler will be used to invoke the proxy method.
Participant b = new Participant("B").start();
EntityExample proxy = (EntityExample) b.getEntity("A1",0);
String name=proxy.getName();
handler = (EntityExample_I)proxy.getHandler();
handler.printMsg_TCPP("hello 3.");
4 Results
The framework substantially reduced the complexity associated to maintaining a shared state and the number of specialities needed to implement a Distributed Simulation.
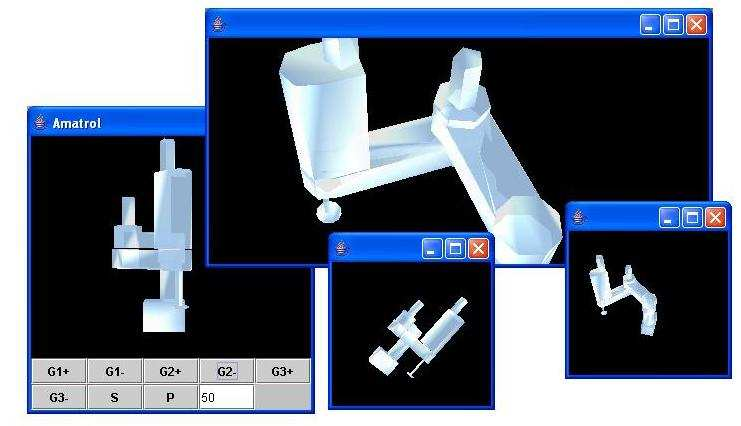
Figure 5: Amatrol Robot implemented using Proxy Model and Java3D, every window is a different participant; each participant sees its entities and the proxies from other participant’s entities.
Figure 6: Space Ship using Proxy Model and Java3D, every window is a different participant; each participant sees its entities and the proxies from other participant’s entities.
5 Conclusion
There are significant advances in various technologies that plenty justify a paradigm shifting in order to get new designs and implementations.
6 Future Work
Implement a secure loader for the proxy Loader, an various secure protocols for the UDP messages.
Introduce the use of annotations and Aspect oriented techiques for method handling instead of name prefixes.
7 Downloads
Home page: http://oodvs.sourceforge.net
Project page: http://sourceforge.net/projects/oodvs
8 Glosary
OODVS Object Oriented Distributed Virtual Systems
RMI Remote Method Invocation
RPC Remote Procedure Call
TCP Transmission Control Protocol
UDP User Datagram Protocol (broadcast and multicast)
HTTP HyperText Transfer Protocol
RSA A public-key encryption technology
RC4 A variable key-size stream cipher
Dead Reckoning
DIS Distributed Interactive Simulation
NPS Naval Postgraduate School
9 References
- Distributed Interactive Simulation (DIS-Java-VRML) http://faculty.nps.edu/brutzman/vrtp/dis-java-vrml/download.html
- Open DIS http://open-dis.sourceforge.net/Open-DIS.html
- Open Astex Viewer http://openastexviewer.net/web/
- ITESM-CEM, Tesis, "Arquitectura para realidad virtual distribuida con física simulada, poblada de agentes autónomos", Ing. Montserrat Morales, Ph. D Isaac Rudomín,
- NPS, Tesis, "AN AUTOMATED APPROACH TO DISTRIBUTED INTERACTIVE SIMULATION (DIS) PROTOCOL ENTITY DEVELOPMENT", Michael Canterbury, September 1995.
- NPS, "Dial-a-Behavior Protocol" (DBP)
- "Networked Virtual Environments and DIS-Java-VRML Library", NPSNET Research Group, Don Brutzman and Mike Zyda
- NPS, " A NETWORK SOFTWARE ARCHITECTURE FOR LARGE SCALE VIRTUAL ENVIRONMENTS", Michael R. Macedonia, Michael J. Zyda,David R. Pratt,Paul T. Barham,Steven Zeswitz
- NPS, " NPSNET - Large-Scale Virtual Environment Technology Testbed", Michael Zyda*, Don Brutzman, Rudy Darken, Robert McGhee, John Falby, Eric Bachmann, Kent Watsen, Ben Kavanagh & Russell Storms